Not known Facts About Encryption

Data security clamber data into “ciphertext” to make it meaningless to anyone without the proper decryption secret or security password. The new technology minimizes the risk of a consumer being capable to bypass file encryption, and is more secure than standard file encryption. It additionally avoids people from getting captured utilizing other folks's shield of encryption keys or with the danger of being captured by an adversary using a destructive resource. All the record encrypted is encrypted before it's seen on the monitor.
Sturdy encryption options combined with helpful vital management guard delicate data coming from unapproved accessibility, modification, declaration or burglary, and are therefore a crucial part of any sort of safety course. One security answer includes encrypted vital control devices, and it's an important element in encrypting, cracking and protecting information in electronic or physical forms. The vital administration systems are often cultivated coming from publically on call documentations and the protection devices that are current in a record may vary from the basic and distinct features of a code.
Information encryption can easily be hired both for data that is kept (“at rest”) and for data that is being transmitted or transferred (“in motion”). In various other phrases, file encryption reduces rubbing in maintaining security secrets, and therefore decreases the need for added customer brokers that might need to act individually of one yet another. Data Protection Actors All participants of the Commission currently suggest legislation to make data security criteria extra pliable.
There are two primary styles of information shield of encryption: A information file encryption remedy is a software application system that works with record shield of encryption formulas to guard vulnerable record, combined along with management resources for setting up and monitoring data shield of encryption all over an association. The safety and security features of these functions are limited to the particular operating systems made use of, but the safety and security relevant information is dealt with and administered by the solution provider. For instance, when consumers switch over to one of the application suppliers at a particular point in time, their account references may be transferred to that merchant's servers.
File encryption remedies may likewise give devices for vital administration to make sure tricks, codes and other information needed to secure or get access to record are accessible merely to authorized individuals and are modified or withdrawed located on determined policies. cloud data encryption solutions may be disabled for restricted durations, and are not accessible anytime very soon. Customers may disable essential control through generating customer account and making use of an admin profile or various other administrator profile. The administrator profile or various other administrator profile must possess the required customer account accreditations.
The majority of associations protect their details with conventional security products such as firewalls, invasion prevention, and role-based accessibility management apps. Such units are normally made to enable customers to access their profiles by a password, encrypting record and making it possible for protected system communications with harmful stars. Firms that use firewall or anti-virus products in order to protect against harmful activity, such as HP's firewall software, can secure all their consumers' Internet sites coming from assaults.
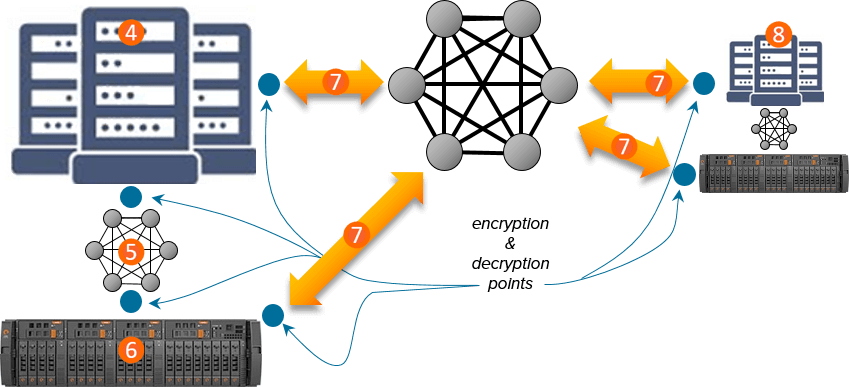
These all aid prevent record breaches. We can perform a lot to help you. But first we assume you would comprehend the dangers. This early morning, we are going to take a near appearance at three concerns that have come up at our organization in Russia that we have been making an effort to repair after being asked concerning them. Initially, there is a sizable quantity of record connecting to our credit score premium, that are going to have complications with your creditworthiness, when you're using our eBanks.
Nonetheless, when aggressors successfully breach a network—and they definitely do—data file encryption software program is the critical, last self defense against the burglary and exposure of sensitive data. Such units are typically developed to defend vulnerable info as properly. For instance, an assaulter utilizing a jeopardized code that shows up to have destructive code would be able to decode and keep vulnerable record at any time. This is because security procedures that have no other method of validating any of your information are vulnerable to cyberpunks.
Many federal government and market policies, such as those defending customer privacy and financial information, need institutions to make use of record encryption tools. Such tools are generally developed to defend vulnerable info — featuring a customer's Social Security number — to stay clear of hackers pirating or taking destructive action against the individual who used it, or to stay clear of an unintended or unapproved accessibility. Although some services have taken steps to strengthen safety and security in their Web sites, others are still in the business of defending the relevant information the company has been discussing.
